“Risk comes from not knowing what you’re doing”
Warren Buffett

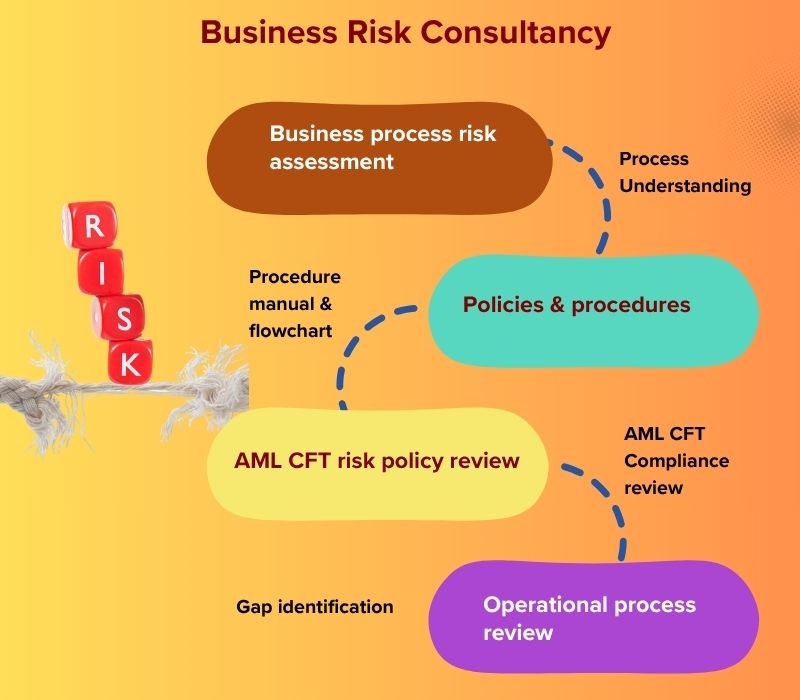
Qualitative Risk Assessment
We evaluate operational risk based on an understanding of your process and its environment on qualitative criteria as likelihood, impact and risk tolerance within Enterprise Risk Management using COSO framework.
Generic Risk Assessment
From our experience across different sectors, we assess your current business process against industry standards for gap identification and solutions and with a bottom to top approach from process owner to management layer.
Technical Risk Assessment
We carry out technical risk assessment to identify and analyse risks unique to operations or area, in the fields of cybersecurity, compliance with regulatory framework, health & safety at workplace.
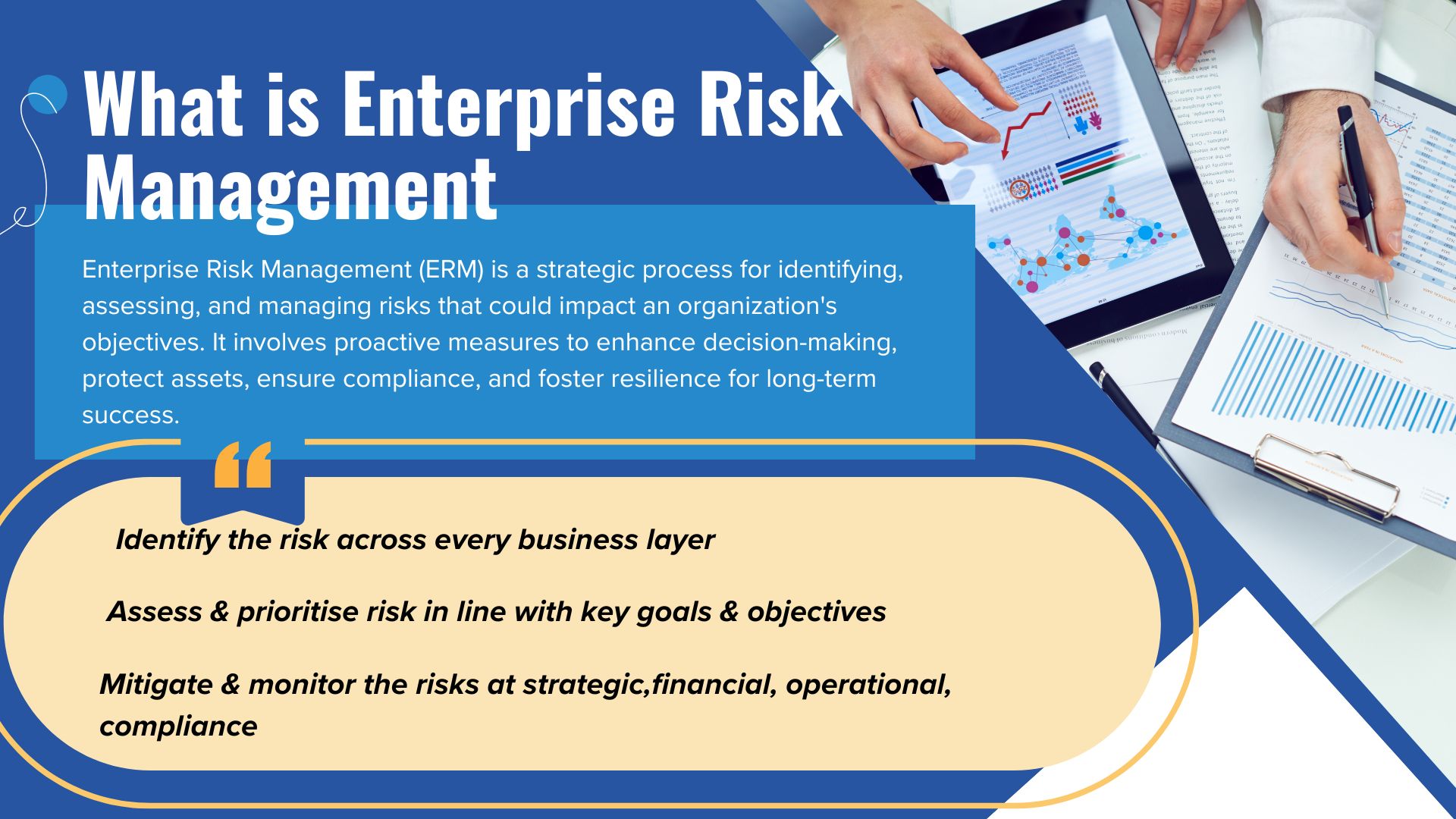
Enterprise Risk Management
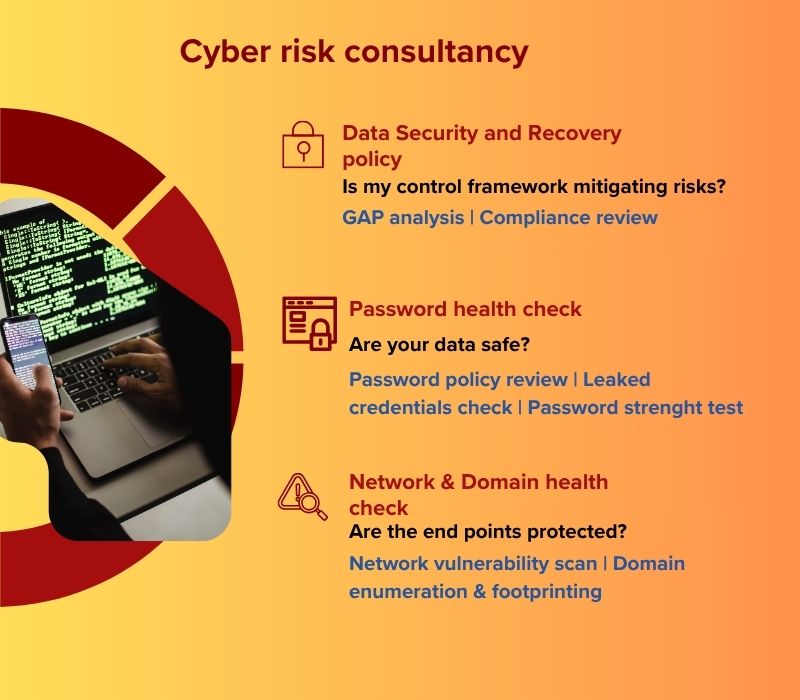
Cyber Threats Assessment
Protecting Your Digital Assets
We assist you in the development of IT security policy & procedure manuals, and help businesses safeguard their digital assets, mitigate risks, and ensure compliance with industry standards and regulations.
We offer a range of comprehensive solutions in vulnerability risk management for IT assets, that bring an additional safeguard for your business’s digital assets and ensure resilience against evolving threats.
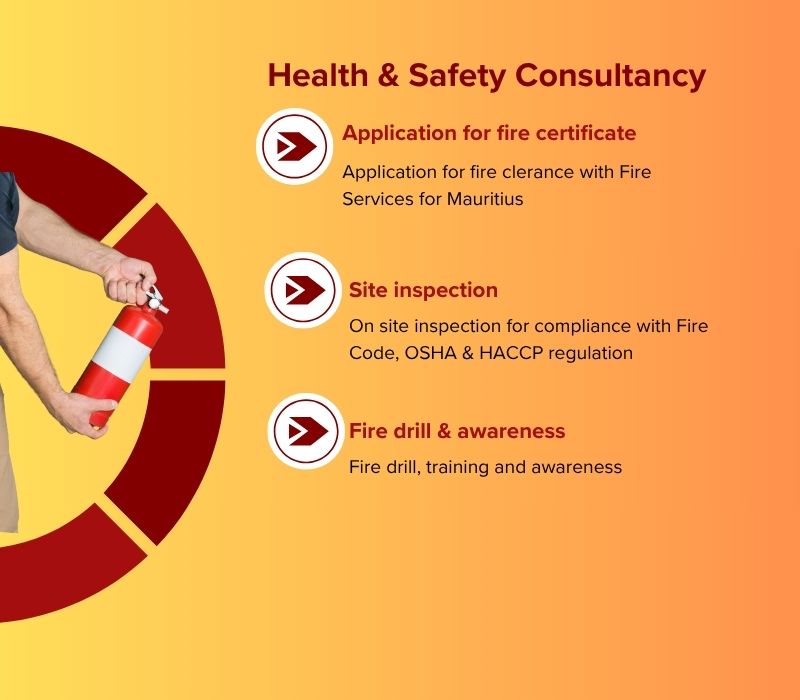
Health & Safety Risk Assessment
Dive into an experience that sets us apart in an ever-evolving landscape.
With our expertise in compliance with fire code requirements and the development of fire security procedures and protocols, we help businesses and organisations ensure the safety of their premises, employees, and assets.
Compliance Risk Assessment
Workplace Safety
We assess compliance with Mauritius Fire Code and OSHA for workplace safety and accompany you in the application process for fire certificate in compliance with Mauritius Fire & Rescue Service Act 2013.
Data Protection
Our experts provide consultancy services in the design of policies and procedures for data protection, data recovery in line with Data Protection Act and FSC requirements for a risk based approach to secure data and PII information.